Description
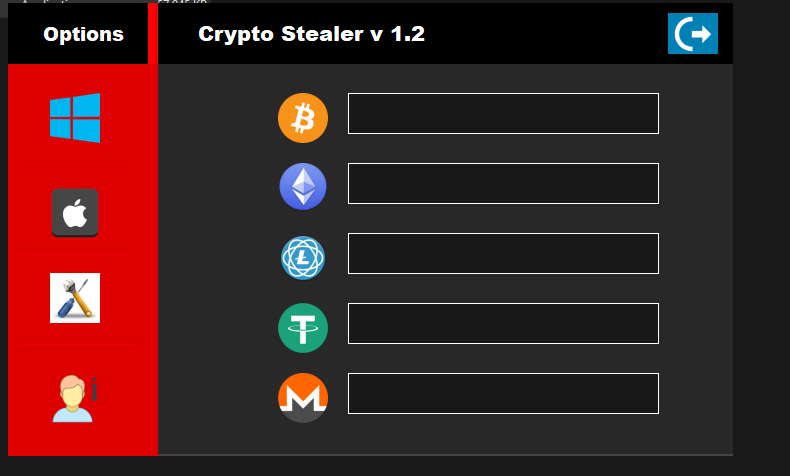
Latest Crypto Stealer v1.2
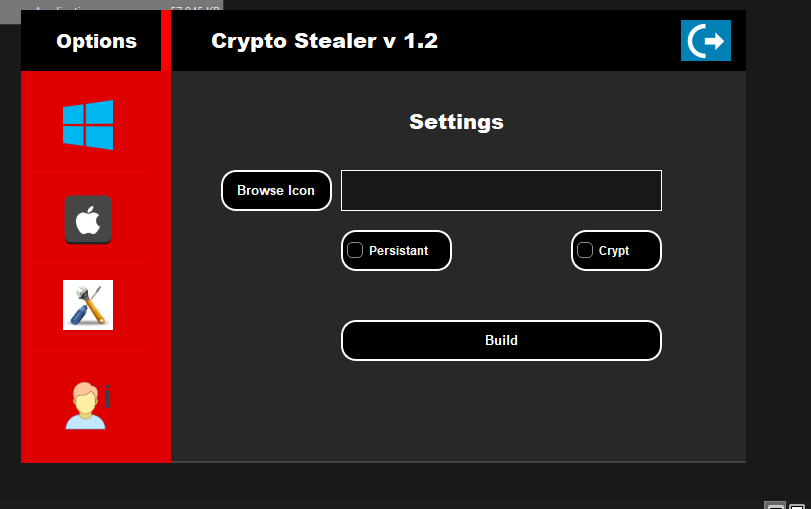
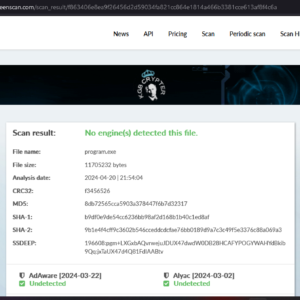
The Crypto Stealer v1.2 is a state-of-the-art, fully undetectable tool designed for ethical penetration testing and cryptocurrency security analysis. This tool enables cybersecurity professionals to test vulnerabilities in cryptocurrency wallets by simulating attacks on BTC, ETH, LTC, XMR, and USDT TRC20 wallets. It bypasses antivirus systems and operates persistently, ensuring that it can deliver results in both Windows and MacOSx environments. This product is for educational use only and should be employed solely in controlled, legal penetration testing environments to identify potential weaknesses in cryptocurrency wallets.
Key Features:
- Supports Multiple Cryptocurrencies: Compatible with BTC, ETH, LTC, XMR, and USDT TRC20.
- Cross-Platform: Generate stealer tools for Windows and MacOSx systems.
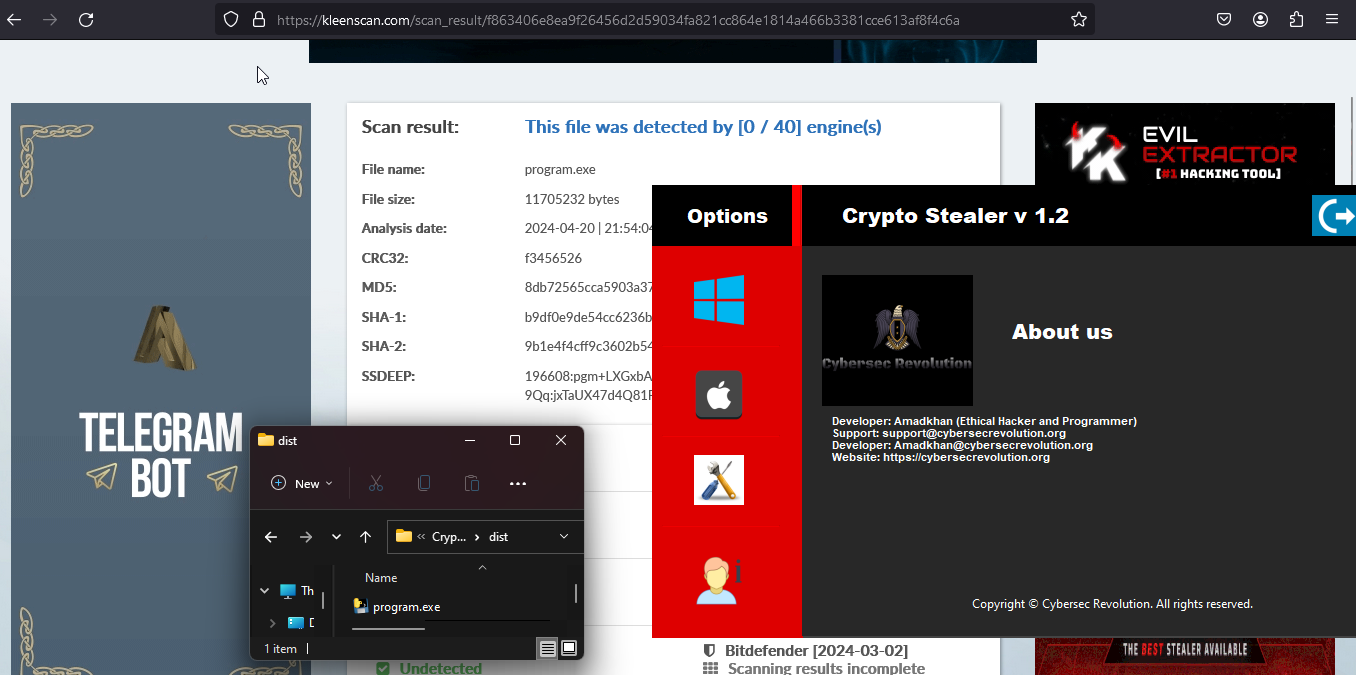
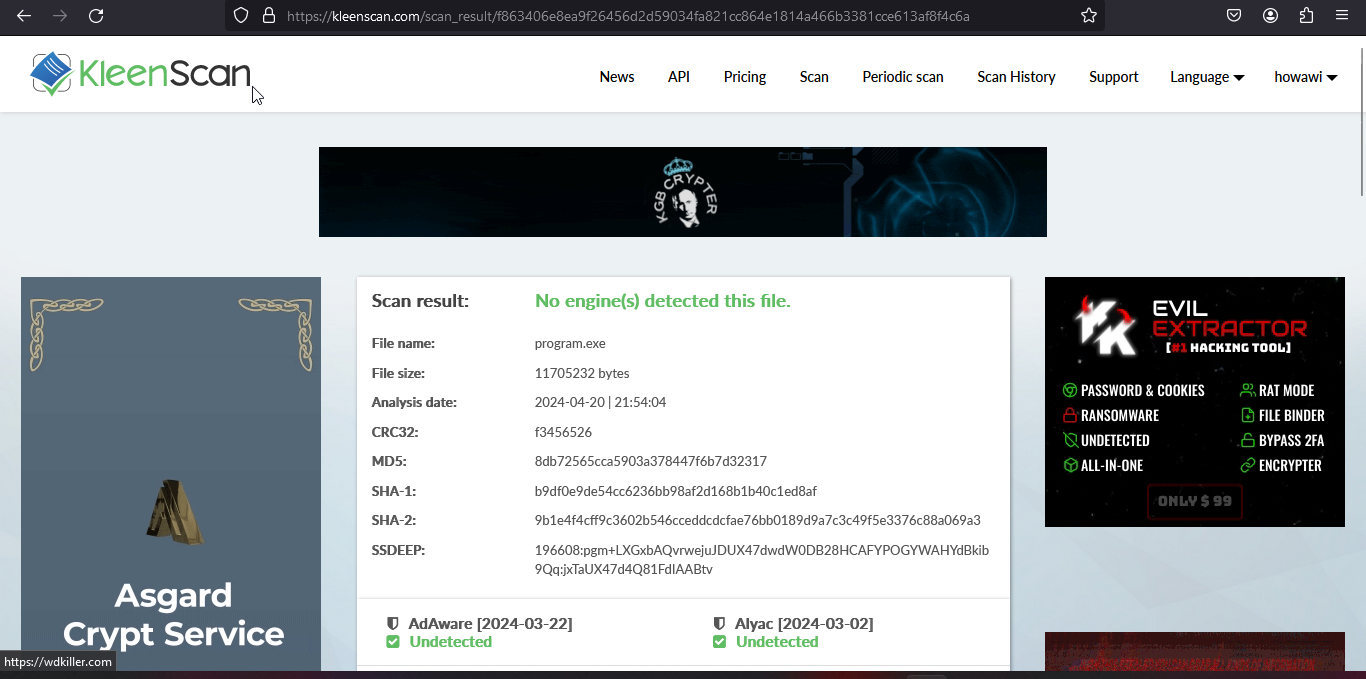
- Fully Undetectable: Bypasses all antivirus protections, making it invisible to security software.
- Persistent: Ensures continuous operation without detection or interruption.
- Default Crypter: Utilizes advanced crypter technology to keep your stealer undetected.
Use Cases:
- Penetration Testing:
- Test the security of cryptocurrency wallets by simulating attacks on wallets such as BTC, ETH, LTC, XMR, and USDT TRC20.
- Vulnerability Assessment:
- Identify weaknesses in wallet configurations and setups for both Windows and MacOSx systems.
- Cryptocurrency Wallet Security Audits:
- Evaluate the effectiveness of wallet protection mechanisms and ensure that cryptocurrency assets are secure from potential threats.
- Educational & Research Purposes:
- Learn and understand the inner workings of cryptocurrency wallet theft methods and the techniques used to bypass security systems.
- Testing Antivirus Evasion:
- Test how well antivirus programs detect and handle malware targeting cryptocurrency wallets in a controlled environment.
- Improving Cryptocurrency Security:
- Utilize the tool in security workshops to showcase how attackers might bypass security measures and steal cryptocurrency, raising awareness about protection strategies.
Legal Disclaimer:
This tool is for ethical use only and intended to be used for security research and penetration testing in a legal, controlled environment. Unauthorized use of this product is illegal and against ethical hacking principles.

Reviews
There are no reviews yet.