Description
Latest Fully Undetectable Logs Stealer – Educational Cybersecurity Tool
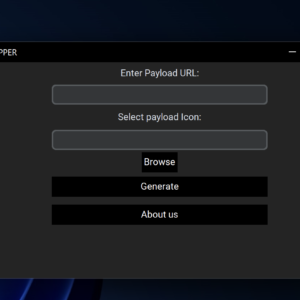
The Logs Stealer is a specialized tool designed for ethical penetration testers and cybersecurity professionals to understand and evaluate how sensitive data such as login credentials, credit card information, and cookies are exposed and can be retrieved by malicious actors. This tool is intended solely for legal and educational purposes, allowing users to learn about information-stealing malware techniques and their detection/prevention methods in a controlled and ethical environment.
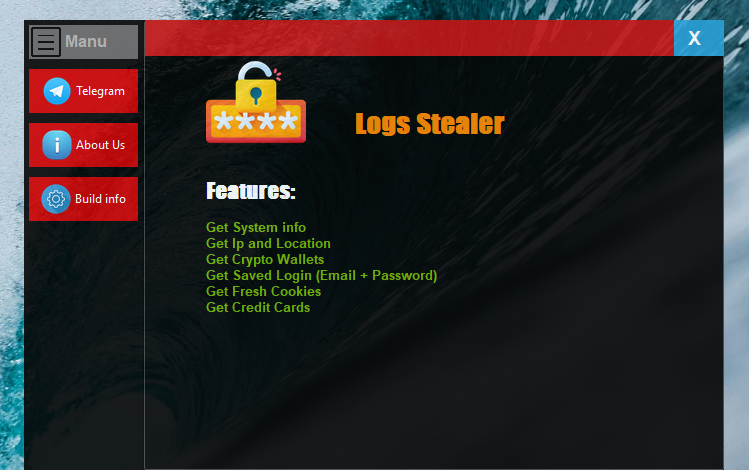
Features:
- System Information: Gather system details to understand what data is accessible to attackers.
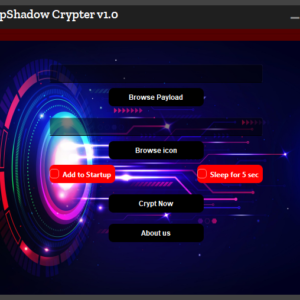
- Undetectable: Operates under the radar of common antivirus and security software, offering insight into evasion tactics.
- IP + Location Info: Capture IP addresses and geographical location for educational analysis.
- Credit Card Info: Learn how credit card data can be exposed through malicious software.
- Login Cookies: Understand how attackers can steal session cookies for unauthorized access.
- Saved Logins: Retrieve saved login credentials (email + password) for educational demonstration.
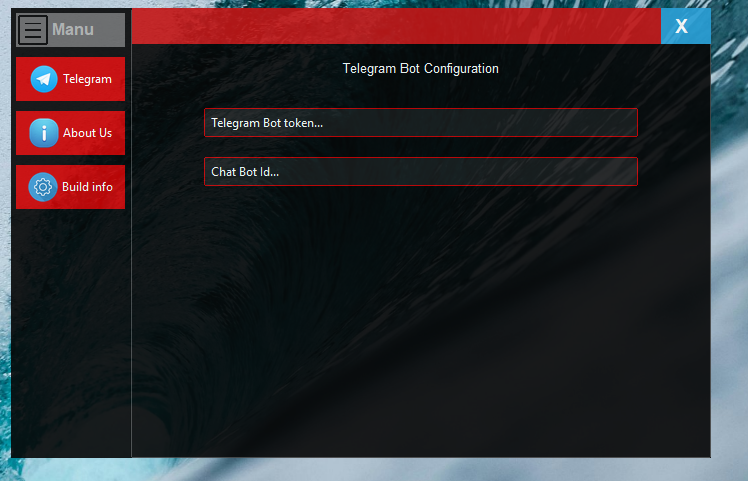
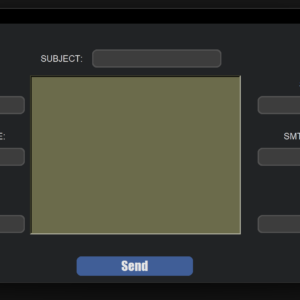
- Result Delivery via Telegram: Get results remotely through Telegram for a better understanding of remote data exfiltration.
Use Cases:
- Penetration Testing: Conduct controlled penetration tests to identify vulnerabilities related to information theft and data exfiltration.
- Cybersecurity Training: Use the tool in training environments to educate students or professionals on how attackers steal sensitive information and how to defend against it.
- Malware Analysis: Analyze the behavior and techniques used by information-stealing malware, and learn how to detect it.
- Security Research: Research undetectable malware techniques and develop better detection methods for real-world use.
- Awareness Campaigns: Demonstrate the potential risks of data theft and how users can protect themselves from malicious software.
Note: This tool is strictly for ethical penetration testing and awareness training in controlled environments.
Reviews
There are no reviews yet.