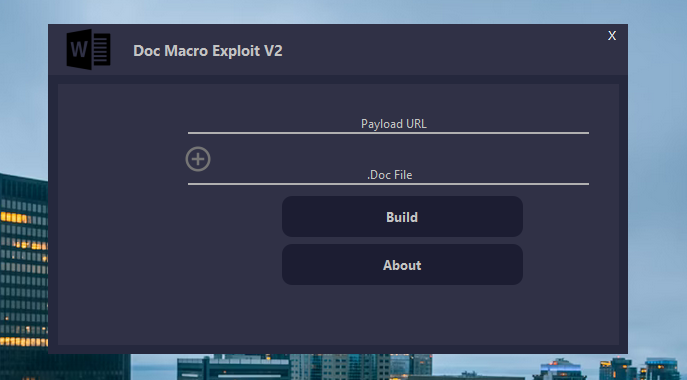
Description
The Microsoft Word Macro Exploit is a powerful cybersecurity tool designed for penetration testers and ethical hackers to assess vulnerabilities in Windows systems that could be exploited through malicious macro execution. This tool simulates the execution of an exploit using Microsoft Word macros to bypass security mechanisms and compromise a target system. Intended for use in controlled, authorized environments, it helps security professionals evaluate the effectiveness of defenses against macro-based attacks and identify potential weaknesses that could be exploited in real-world scenarios.
Features:
- Silent Execution:
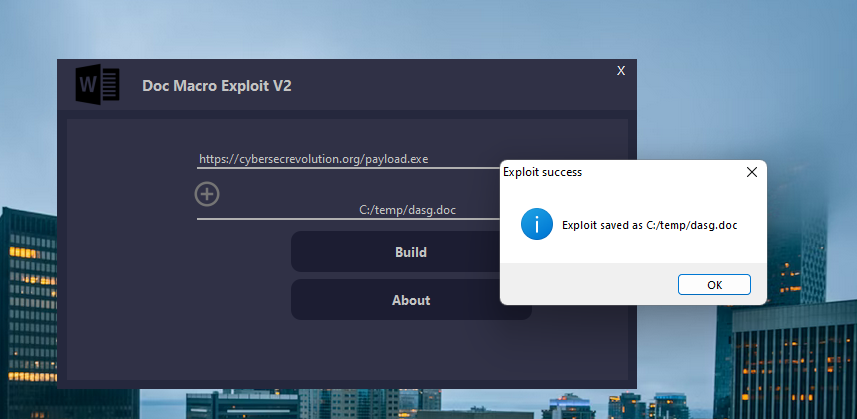
Executes malicious macros silently, mimicking real-world attack scenarios to bypass security controls without triggering alerts or requiring user interaction. - Windows System Compromise:
Leverages macro vulnerabilities to simulate attacks that could result in system compromise, allowing testers to evaluate the system’s resilience to such threats. - Bypass Security Filters:
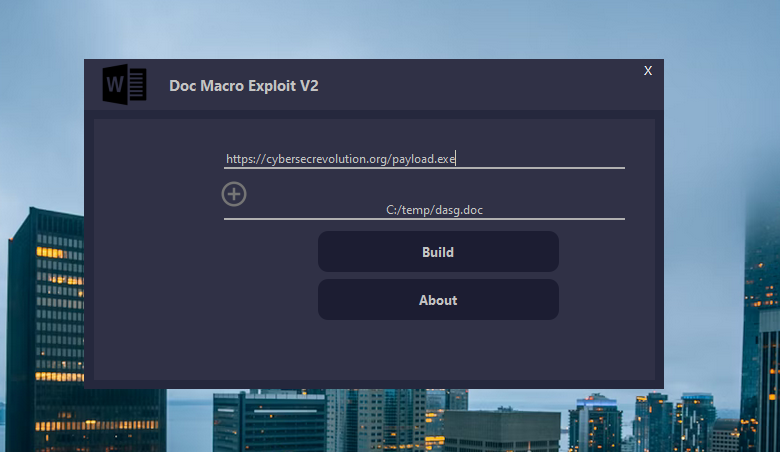
Tests the effectiveness of email and document security filters (such as antivirus software and spam filters) by attempting to execute macros in Office documents. - Cross-Version Compatibility:
Supports Microsoft Office versions up to Office 2019 and earlier, ensuring compatibility with a wide range of Windows environments for comprehensive security assessments.
Use Cases:
- Penetration Testing for Windows Systems:
Assess vulnerabilities in Windows systems by testing how they handle malicious macros in Office documents. - Security Filter Evaluation:
Test the ability of email security filters and antivirus programs to detect and block macro-based exploits. - Compromise Simulation:
Simulate a real-world attack to determine whether a system can be compromised by exploiting macro vulnerabilities in Microsoft Word documents. - Vulnerability Assessment and Remediation:
Identify weaknesses in the system’s defenses and help organizations patch vulnerabilities to mitigate future risks.

Reviews
There are no reviews yet.